Automation to block malicious flows detected by Azure Traffic Analytics | by James Dumont le Douarec | Microsoft Azure | Medium

The Irish National Lottery on Twitter: "Due to high traffic volumes, we are experiencing some technical difficulties with our website and app. We apologise to any players who may have been impacted.
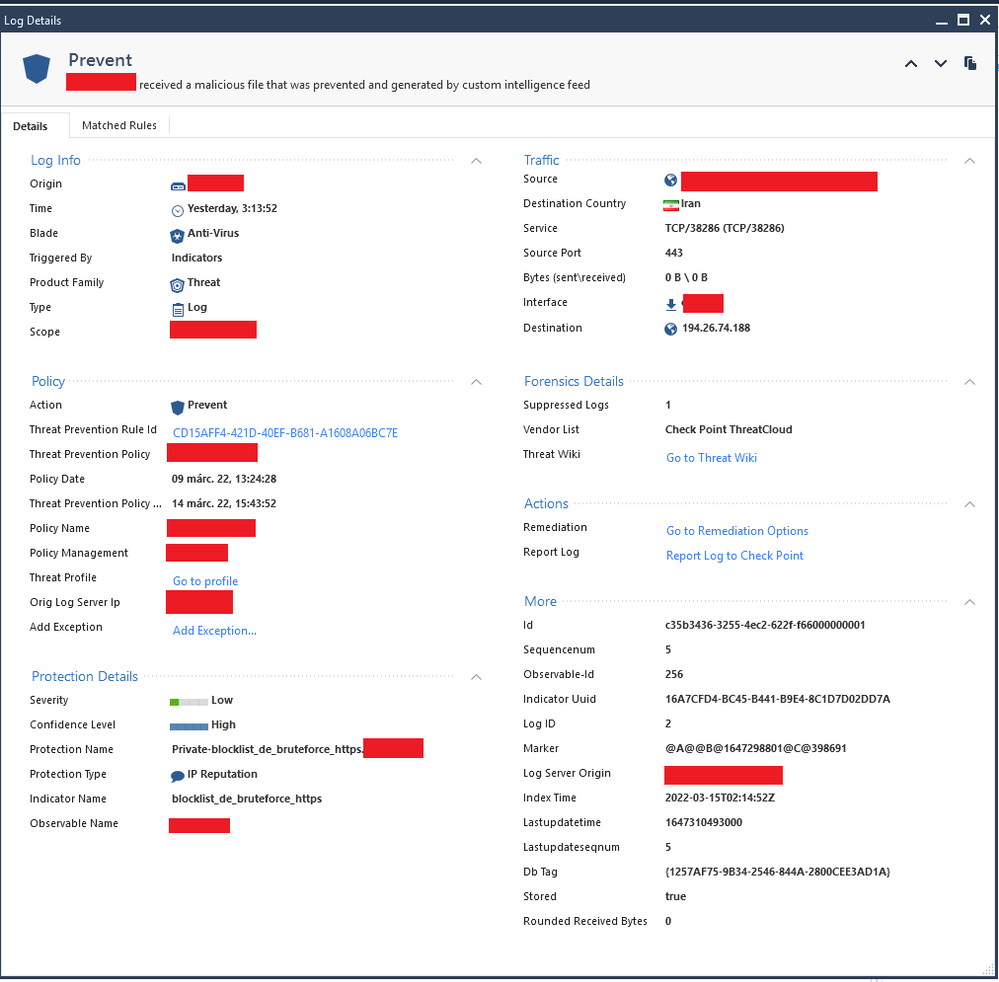
Exporting CSV Traffic Logs Fails to Download Completely on PA-2... - Knowledge Base - Palo Alto Networks

InApp Mysql VS Azure Database for MySQL Which one is faster for Woocommerce Wordpress website ? - Microsoft Q&A

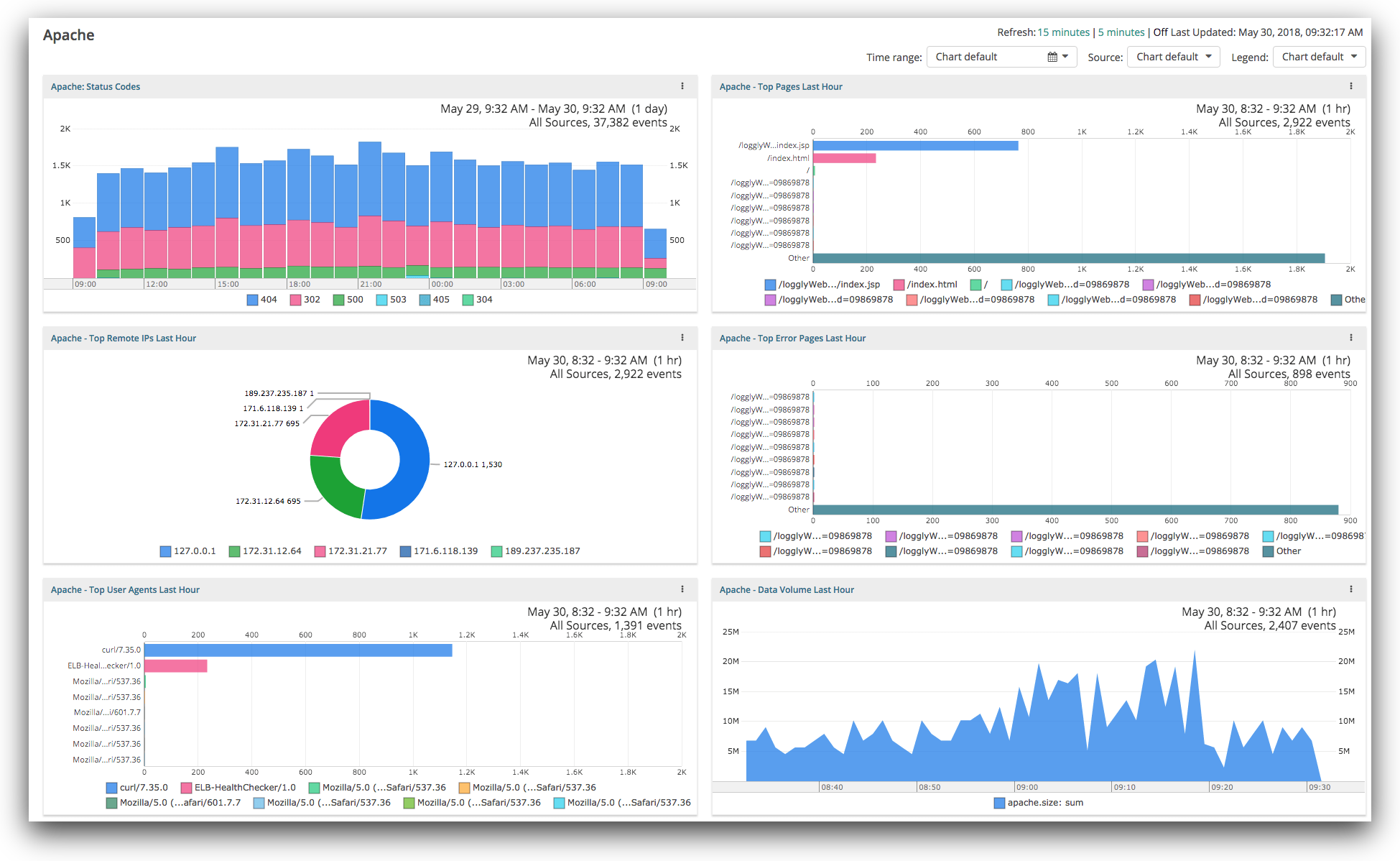
Enterprise Application Logging Best Practices (A Support Engineer's Perspective) | by Thilina Ashen Gamage | Better Programming
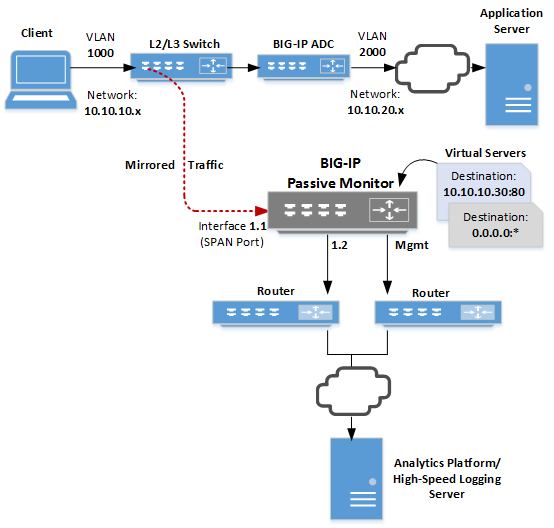
AskF5 | Manual Chapter: Configuring the BIG-IP System for Passive Monitoring,Configuring the BIG-IP System for Passive Monitoring,Configuring the BIG-IP System for Passive Monitoring,Configuring the BIG-IP System for Passive Monitoring,Configuring the ...